![PDF] BTG-BIBA: A Flexibility-Enhanced Biba Model Using BTG Strategies for Operating System | Semantic Scholar PDF] BTG-BIBA: A Flexibility-Enhanced Biba Model Using BTG Strategies for Operating System | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/83fcec720b425bbc4e764ff167afaea6721dbb3e/4-Figure2-1.png)
PDF] BTG-BIBA: A Flexibility-Enhanced Biba Model Using BTG Strategies for Operating System | Semantic Scholar

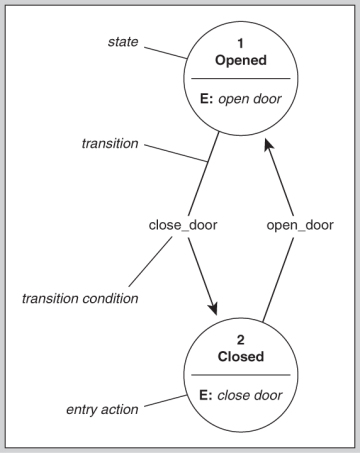
Two Laws of Biba Model The satisfaction of both Biba laws, prevents the... | Download Scientific Diagram

Improved Biba model based on trusted computing - Liu - 2015 - Security and Communication Networks - Wiley Online Library

CISSP PRACTICE QUESTIONS – 20210401 by Wentz Wu, CISSP/ISSMP/ISSAP/ISSEP,CCSP,CSSLP,CISM,PMP,CBAPWentz Wu

Biba Integrity Model Ppt Powerpoint Presentation Outline Graphics Example Cpb | Presentation Graphics | Presentation PowerPoint Example | Slide Templates

Two Laws of Biba Model The satisfaction of both Biba laws, prevents the... | Download Scientific Diagram